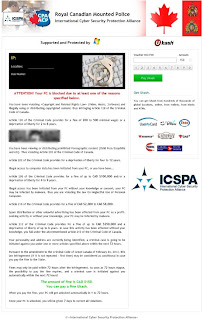
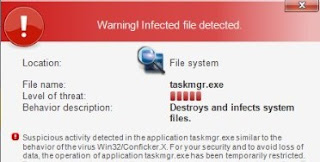
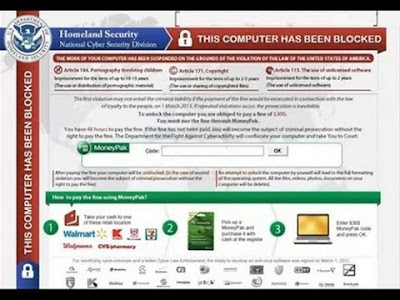
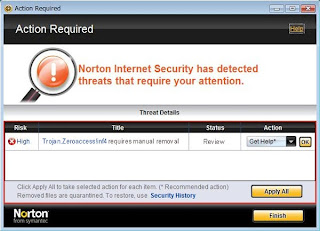
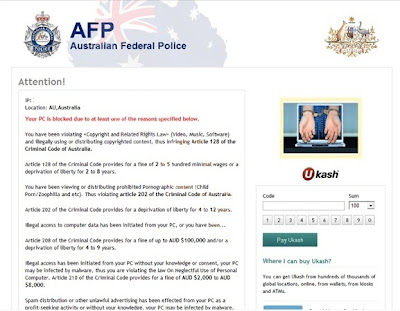
HEUR:Exploit.Java.CVE-2013-2423.gen is defined as a malignant Java Script virus that coercively changes system settings and slow down computer performance. As a Java Trojan, HEUR:Exploit.Java.CVE-2013-2423.gen does not penetrate into computer straightly. It always makes use of fake Java programs to bypass the block of antivirus software and download into computer successfully. Thousands of users who have been infected with HEUR:Exploit.Java.CVE-2013-2423.gen are all complaining for the stubbornness of the virus. Indeed, it is protected by advanced tactic that common antivirus software won’t be able to remove it easily and completely.

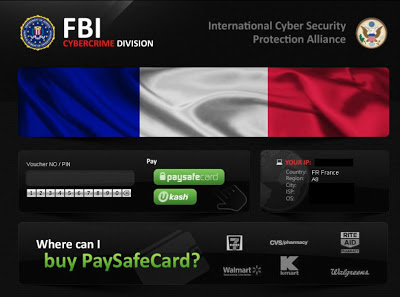
Needless to say, HEUR:Exploit.Java.CVE-2013-2423.gen is very dangerous to system files. It has the capability to damage system files and block programs to cause system chaos. HEUR:Exploit.Java.CVE-2013-2423.gen also adds executable codes on system, exploiting Internet vulnerabilities for getting computer from being injected with other severe malware. Leaving the virus on system, it is very probably for computer crashing down. Thus, it is important to exterminate HEUR:Exploit.Java.CVE-2013-2423.gen from your computer in time.